Hello,
Let's go on for PS3 Hacking part 2 :).
FAQ! Frequently Asked Questions
Why do everybody want the lv0 keys so badly even though they might not know how to use them?
WAREZ ... WAREZ ... EVEN MORE WAREZ ...
Homebrew has been attain with firmware <= 3.55 ... so heh ;).
Personnaly, I'm not interested in CFW ... more interested in the technical details than anything else here :).
Why nobody want to release the lv0 keys?
Really you're asking this question? ... Reread first question ... and look at geohot's legals problems back in January ;).
Basically, you released these keys and Sony will sue you to death ... :s.
Huh ok ... how does having lv0 keys allow us to have custom firmwares if we don't have actual loaders private keys (for signing)?
As waninkoko explained, we don't need the ldr private keys (as long as we have the earliest ldr keys ;)).
We decrypt everything using the first loader key (either metldr < 3.60 or lv0 >= 3.60), make the wanted modifications. Afterward, we can change all the public keys (and thus we would have our private keys), re-encrypt them all. Done you've got a custom firmware.
Waninkoko Speaks About Creating v3.61 CFW
How do they disallow homebrew on newer firmwares then if we can still sign it and that they can't revoke the keys?
They make use of whitelisting. They reference each and every games that were made for the PS3 ... any games not in there will not get launched.
Here a place where they speak about PS3 whitelisting: http://psx-scene.com/forums/f118/application-whitelist-96728/
For an explanation of what are the differences of whitelisting and blacklisting here: Whitelisting vs. Blacklisting
Moreover, they can change most keys they want on the latest hardware revisions. But since the update file "has to be" compatible with older hardware ... any currently manufactured hardware could be theoretically pawned.
For people wondering why the PS3 can not be totally resecured
Mathieulh's thoughts on resecuring the PS3: PS3 3.56 Firmware A Minor Drawback To Hackers .
Basically, the problem Sony encounter while trying to resecure the PS3: compatibility.
The boot chain integrity has been compromised so possibility to reflash externally in order to run unsigned code.
They could try to have 2 files for updates:
- 1 file for the old consoles
- 1 file for the new consoles
Would it be a possibility to "resecure" the PS3? Maybe ... who knows?
If that is the case, only the new PS3 (changed keys, changed hardware revision, etc) would be secured again. Old console ... no way.
(to be continued ...)
That's it for now,
You've got everything needed to understand PS3 actual pawning state ;),
Cheers,
m_101
mercredi 16 novembre 2011
PS3 Hacking (Part 1) - Exploitation
Hello,
It's been a long time since the last time I posted :), I miss hacking bits and binaries ... but well, I read a bit for relaxing ... here it is :).
Anyway, I've been reading about PS3 a bit and it's funny to see that not a single PS3 specialized news site has been able to correctly understand the exploits they publish on a regular basis.
I have not tried to hack the PS3 yet, just reading documentation on it just out of curiosity so if any info here is wrong, do not hesitate to correct me in the comments ;). I will gladly fix any errors :).
Let's start with a bit of history.
PS3 hacking history
The PS3 got out for general consumption in 2006, but wait wait wait ... wtf is that secure system? Oh yeees! Linux compatible!
2007 ... 2008 ... 2009 ... nothing until ... 2010.
In 2010, GeoHot just played a bit with it to see what the security of the PS3 is worth ... and he managed to bypass the hypervisor and dump it using a hardware glitch trick (used for analyzing smartcards) and some virtual page management trickery (playing with HTAB and all ;).
He did it for fun ... Sony did not like it: OtherOS banned from the console!!!
Here within started the PS3 epic fail story ^^. They shouldn't have taken out OtherOS ...
Basically:
GeoHot's glitch exploit -> PSJailbreak 1 -> fail0verfl0w key calculation hack (Sony Epic Fail) -> metldr keys dumped by GeoHot -> ???
The metldr key basically allows to decrypt all ldr.
Before going into the boot order (and explain what the metldr keys fuss was all about), let's review basics of the PS3 crypto.
PS3 Cryptography 101
All the PS3 crypto is done in "isolation" using the CELL CPU as explained here: The Cell Broadband Engine processor security architecture .
The PS3 make use of AES256CBC, AES128CTR for encryption and decryption.
For the signatures, it makes use of HMAC-SHA1 and ECDSA.
Sony managed to do an EPIC FAIL yes.
Basically in Sony's ECDSA implementation, fail0verfl0w managed to find a flaw that allowed to compute private keys using simple algebra.
Instead of using a random k, Sony used a constant ...
If k is not random, we have this equation:
s − s' = k − 1(z − z')
Then we can compute k:

Since we have k, we can compute the private key dA:
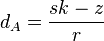
For more details: PS3 Epic Fail . Their presentation is quite interesting as it includes history of past hacks, how the SELF crypto" works and how to compute PS3 private keys (for <= 3.55) :).
For SELF file format understanding: SELF File Format and Decryption and PS3 Epic Fail .
Reminder for ECDSA: ECDSA .
So yeah basically, all the current hacks are first based off on GeoHot's and fail0verfl0w stuffs (seems like they did not get the credit they deserved).
Now that you have the background for the crypto" and the SELF file format, let's go on with the boot order :).
Boot Order
Every steps of the PS3 is encrypted (but the first step obviously).
My theory is that the first thing that decrypt the first loader is in plaintext either in software or hardware ... you can not run encrypted code directly, you first need to decrypt it ;). Thus the best place to hide this thing would be the CPU itself (if you store it in a chip on the motherboard ... game over). Unless you have some hardcore silicon hacking lab at disposal ... even you if you do.
Prove me wrong (that encrypted code can run directly on a CPU without decryption ...) ...
The boot order before 3.60:
syscon -> bootldr -> lv0 -> metldr -> lv1ldr -> lv1 -> metldr -> lv2ldr -> lv2 -> metldr -> appldr -> metldr -> isoldr -> metldr -> rvkldr
The bootldr and metldr are encrypted by a Hardware Key which is defined by console (that is one of the reason they can not be updated).
The metldr keys released by GeoHot basically allows us to decrypt all the ldrs, re-encrypt them and thus bypass any security measure.
The earlier you are in the chain, the more steps you control since all the afterhand ldr depends on previous ldrs.
The boot order after 3.60:
Damn, they changed the boot order a little bit (which makes a huge difference :p).
They "suppressed" metldr and replaced it by lv0.
lv0 now serve as the metaloader. Obviously the clever thing to do (from an engineering standpoint) is to reuse some of the metldr code and change the keys (we don't know if they did that as of now).
They could not update the metldr ... but since lv0 is updatable and run before metldr ... they removed metldr.
lv0 and below have not yet been exploited (publicly).
As soon as these get exploited (we get lv0 keys) then game over for real for the PS3.
The bootldr can not be updated and below it ... you can not update anything either (without breaking compatibility).
Theoretically, we could get lv0 private keys as old consoles were produced when Sony used their failed crypto :) (look in Mathieulh's tips section below ;)).
PS3DevWiki - Boot Order
As you can see, we have a chain of trust, so if you compromise a loader in the chain, you possibly compromised the rest of the chain ;).
Okay, let's talk about the current exploits.
Exploited vulnerabilities that would kill the Sony PS3
Before trying anything, to be on the safe side, be sure to have: Hardware Flashing in case you mess up anything that can be recovered ;).
You WILL end up with a BRICK if you are not careful and do not know what you are doing.
Mathieulh's leaked metldr exploit
Mathieulh's technical explanation of the leaked metldr exploit: How to pwn metldr the "easy" way .
More info on dumping metldr: here.
Mathieulh's tips and/or clues
He gave us many tips so people start looking: Stop bitching and whining .
"If you can exploit loaders, you can patch them on the fly and remove the signature checks, on the other hand of you dump the bootloader keys, you can also calculate the private key for lv0."
"The bootloader cannot be updated, as such the bootloader keys that decrypt lv0 cannot be changed on existing consoles, thus they remain the same since 1.00"
"The metldr keys aren’t the keys that sign metldr, they are the keys that are stored within metldr’s binary."
"In fact metldr and the bootloader aren’t selfs, as such they are signed and encrypted with different algorithms than the rest of the ps3 binaries."
Decrypt Or Dump LV0 For 3.60 CFW+ Exploit – Mathieulh
Mathieulh give hints to exploiting v3.60, talks about graf_chokolo, and Rebug
The bootloader can be reloaded multiple times: @fail0verflow I don't really care about the ps3 anymore anyway. Here is a protip before I am gone, you can load the bl more than once.
He exploited this glitch : CELL Reset Exploit as he expressly say here: Mathieul's tweet .
Dumps screenshot
About EID: EID IS NOT CODE
Other clues
RMS spoke a bit about lv0: here.
“Exploiting” firmware v3.60 (or 3.56) yourself using leaked blueprints
How to find v3.60+ Keys By SouL & DemonHades
Until someone has the balls or is crazy enough to release the exploit, obtained keys ...
And ... fail0verfl0w are coming back for 28c3 in December this year: here. We'll see what they prepared for us ;).
Just so we are clear: it mainly concerns currently released PS3, Sony is capable to release new hardware revisions that would change any keys they want. They don't do it since they release only one firmware update (so this file has to be compatible with old PS3 and new PS3).
Summary
Ok now you should have a better idea as where the current state of PS3 hacking is.
lv0 is the target, multiple clues have been given. Now more knowledge is needed to dig into it ;).
If you get lv0 keys (private and public) then it means you're also able to get it's keys. So you'll be able to sign a custom lv0 and thus execute code to go deeper and find holes.
The thing is: lv0 is so low level that ... you could brick your PS3 easily with any mistake(s) you make :s.
Anyway, I don't see the purpose of the CFW 3.60+ as we already have CFW for 3.55 => homebrew is there to stay. If people want the CFW 3.56+ so badly it's for warez ...
(to be continued ...)
m_101
Inscription à :
Articles
(
Atom
)